Bad News to Ransom Payers: 80% of You Will Face a Second Attack Within 30 Days

New insight into what happens during and after a ransomware attack paints a rather dismal picture of what to expect from attackers, your executives, and your operations.
I’d love to tell you that once you get through a ransomware attack, all will be well. But that’s just not the case. According to CyberReason’s Ransomware: The True Cost to Business report, the reality of mid- and post- ransomware attack circumstances are anything but resilient.
Let’s start with the fact that, according to the report, 73% of all organizations have experienced a ransomware attack in the last 12 months. And of those that were attacked, the question of paying whether the ransom was paid always comes up:
- 41% paid to “expedite recovery”
- 28% paid to “avoid downtime”
- 49% paid to “avoid a loss in revenue”
But even after paying the ransom, 80% experienced a second attack and 68% were asked for a higher ransom!
Then there is the aftermath to the organization:
- 54% still had corrupted systems or data
- 37% had to lay off employees
- 35% had a C-level resignation
- 33% had to temporarily suspend business
What’s interesting is that 75% of organizations believe they have the right contingency plans to manage a ransomware attack – a number that hasn’t changed in the last year, according to CyberReason. This data point mixed with the aftermath stats above makes me think of the old adage “The best-laid plans of mice and men often go awry.”
So, while your organization “has a plan” to address ransomware, the only truly effective plan is to attempt to stop it all – a strategy that needs to include empowering your users with Security Awareness Training so they are able to distinguish legitimate email and web content from malicious content intent on kicking off a ransomware attack.
Free Ransomware Simulator Tool
Threat actors are constantly coming out with new strains to evade detection. Is your network effective in blocking all of them when employees fall for social engineering attacks?
KnowBe4’s “RanSim” gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 22 ransomware infection scenarios and 1 cryptomining infection scenario and show you if a workstation is vulnerable.
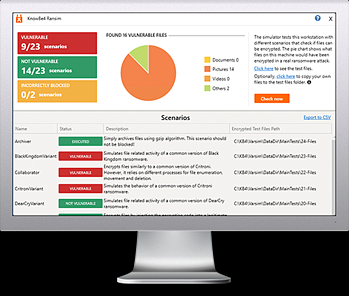
Here’s how it works:
- 100% harmless simulation of real ransomware and cryptomining infections
- Does not use any of your own files
- Tests 23 types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/ransomware-simulator-tool-partner?partnerid=001a000001lWEoJAAW

