“Browser-in-the-Browser” Phishing Technique Spotted in New Steam Account Attack

Luring victims using a realistic- and legitimate-looking fake browser window to steal Steam accounts, this new type of social engineering may be a sign of things to come.
I’ve long written about impersonated brands, fake websites, and spoofed logon pages in countless phishing scams and attacks. But this one separates itself a degree of sophistication higher than anything you’ve seen thus far, potentially resetting the bar for future social engineering attacks.
According to security researchers at GroupIB, the new technique – dubbed “Browser-in-the-Browser” – pops up looking like a new window used for authentication; only it’s actually part of the initial malicious site. In the example below, users of the gaming platform Steam are messaged with appealing Steam-related offers (such as participating in a tournament) that would likely require authenticating to Steam. Once on the page with the supposed offer, a new window appears to pop-up asking the user to authenticate.
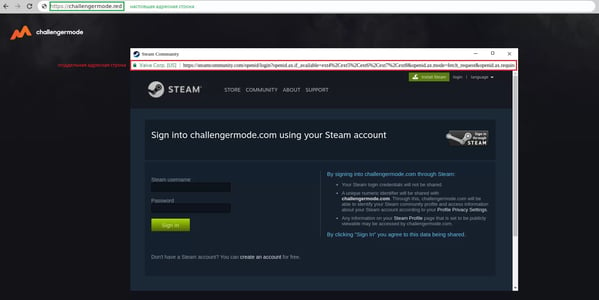
Source: GroupIB
Look at the details in the screenshot – what looks like a valid URL is place in the “window” along with a green lock, indicating a proper SSL cert. If you didn’t know better (and now you do), you’d think it was legitimate. What’s actually happening is there is no new window; it’s just a very impressively-designed in-site page that collects credentials and even additional “windows” for two-factor authentication needs.
What makes this attack so very dangerous is its’ potential. Think about anytime you use third-party authentication (such as Google, Facebook, Microsoft 365, or any cloud-based directory service) – this same technique could be used to trick users into providing business credentials.
The answer here isn’t to tell users “always double-check it’s a real window” – that’s not the issue; what is good advice (which is taught as part of continual Security Awareness Training) is to never engage with unsolicited messages (whether across email, social media, or in-platform messaging of any kind), as cybercriminals are always looking for new (and do I need to say innovative after you’ve read all this?) ways to fool you out of your credentials.
Request A Demo: Security Awareness Training
New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn’t a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4’s security awareness training and simulated phishing platform and see how easy it can be!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/one-on-one-demo-partners?partnerid=001a000001lWEoJAAW

