DarkSide Ransomware Returns as BlackMatter After Sudden Shutdown of Operations

Probably the world’s most notorious ransomware gang disappears completely and subsequently reappears with new branding in an attempt to separate themselves from the types of attacks that originally brought them fame.
Darkside was the group behind most of the recent attacks on critical infrastructure companies in the U.S. and even faced scrutiny from the U.S. Government. After being shut down in May, the group announced it would shut down operations. What has turned out to be a law enforcement exercise that recovered most of the bitcoins paid in the attack on Colonial Pipeline, seems to have made a loud statement by the U.S. to the DarkSide folks: stay away from our critical infrastructure.
From the ashes rises BlackMatter – encryption algorithms were the giveaway – a rebranding of DarkSide with a clear message that they are officially not attacking specific types of businesses that would put them back into the same mess. From their BlackMatter website on the dark web:
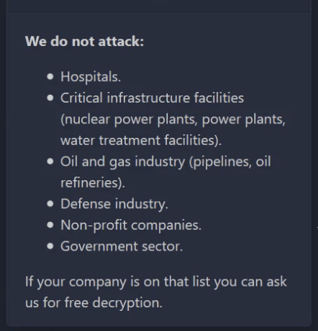
Source: BlackMatter
It appears that even cybercriminal gangs learned their lesson. And, while not giving up their life of crime, they know now to steer clear of targets that will put a cyber target on their back.
Despite the rebranding and new focus, DarkSide/BlackMatter has proven itself to be a dangerous criminal organization with state of the art ransomware capabilities that every organization (including those on the list above!) needs to avoid at all costs.
Free Ransomware Simulator Tool
Threat actors are constantly coming out with new strains to evade detection. Is your network effective in blocking all of them when employees fall for social engineering attacks?
KnowBe4’s “RanSim” gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 22 ransomware infection scenarios and 1 cryptomining infection scenario and show you if a workstation is vulnerable.

Here’s how it works:
- 100% harmless simulation of real ransomware and cryptomining infections
- Does not use any of your own files
- Tests 21 types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/ransomware-simulator-tool-partner?partnerid=001a000001lWEoJAAW

