North Korean Phishing Campaign Targeting Think Tanks, Academics and Media

The U.S. and South Korean governments have issued a joint advisory outlining a North Korean phishing campaign, The Register reports. The threat actor, known as “Kimsuky,” is targeting “individuals employed by research centers and think tanks, academic institutions, and news media organizations.”
“Currently, the U.S. and ROK Governments, and private sector cyber security companies, track a specific set of DPRK cyber actors conducting these large-scale social engineering campaigns as Kimsuky, Thallium, APT43, Velvet Chollima, and Black Banshee,” the advisory states. “Kimsuky is administratively subordinate to an element within North Korea’s RGB and has conducted broad cyber campaigns in support of RGB objectives since at least 2012. Kimsuky actors’ primary mission is to provide stolen data and valuable geopolitical insight to the North Korean regime.”
The threat actors impersonate real people to establish trust with their targets, and eventually trick them into downloading malware. They also collect information by simply conversing with their victims.
“Notably, victim responses to spear phishing lures also provide Pyongyang with the added benefit of insight into foreign policy circles. This covert collection against the community of DPRK watchers is probably of high value to the Kim regime and provides another channel of information on top of what it gains through computer network operations,” according to the joint advisory.
The advisory stresses that organizations shouldn’t assume that they won’t be targeted by these threat actors.
“Some targeted entities may discount the threat posed by these social engineering campaigns, either because they do not perceive their research and communications as sensitive in nature, or because they are not aware of how these efforts fuel the regime’s broader cyber espionage efforts,” the agencies state. “However, as outlined in this advisory, North Korea relies heavily on intelligence gained by compromising policy analysts. Further, successful compromises enable Kimsuky actors to craft more credible and effective spear phishing emails that can be leveraged against more sensitive, higher-value targets. The authoring agencies believe that raising awareness of some of these campaigns and employing basic cyber security practices may frustrate the effectiveness of Kimsuky spear phishing operations.”
New-school security awareness training can give your organization an essential layer of defense by teaching your employees to recognize social engineering attacks.
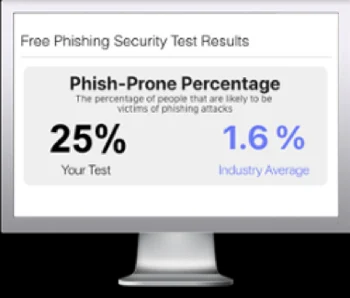
Free Phishing Security Test
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Here’s how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/phishing-security-test-partner?partnerid=001a000001lWEoJAAW

