78% of Ransomware Victim Organizations Encounter Additional Threats-Turned-Extortions

New data sheds light on how likely your organization will succumb to a ransomware attack, whether you can recover your data, and what’s inhibiting a proper security posture.
You have a solid grasp on what your organization’s cybersecurity stance does and does not include. But is it enough to stop today’s ransomware attacks? CyberEdge’s 2023 Cyberthreat Defense Report provides some insight into just how prominent are ransomware attacks and what’s keeping orgs from stopping them
According to the report, in 2023:
- 7% of organizations were victims of a ransomware attack
- 7% of those paid a ransom
- 73% were able to recover data
- Only 21.6% experienced solely the encryption of data and no other form of extortion
It’s this last data point that interests me. Nearly 78% of victim organizations experienced one or more additional forms of extortion (CyberEdge mentions threatening to publicly release data, notifying customers or media, and committing a DDoS attack as example additional threats mentioned by respondents).
IT decision makers were asked to rate on a scale of 1-5 (5 being the highest) what were the top inhibitors of establishing and maintaining an adequate defense. The top inhibitor (with an average rank of 3.66) was a lack of skilled personnel – we’ve long known the cybersecurity industry is lacking a proper pool of qualified talent.
In second place, with an average ranking of 3.63, is low security awareness among employees – something only addressed by creating a proper security culture with Security Awareness Training at the center of it all.
Free Ransomware Simulator Tool
Threat actors are constantly coming out with new strains to evade detection. Is your network effective in blocking all of them when employees fall for social engineering attacks?
KnowBe4’s “RanSim” gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 22 ransomware infection scenarios and 1 cryptomining infection scenario and show you if a workstation is vulnerable.
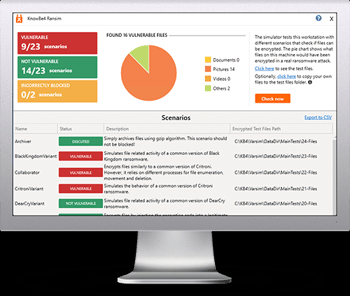
Here’s how it works:
- 100% harmless simulation of real ransomware and cryptomining infections
- Does not use any of your own files
- Tests 23 types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/ransomware-simulator-tool-partner?partnerid=001a000001lWEoJAAW

