A Close Call – PayPal Scam Warning

On Sunday, I received an urgent message from a friend. PayPal had sent him an email saying that a co-worker had sent him money. This was not unexpected, as he was collecting contributions towards a farewell gift for another coworker. What struck him as odd were the instructions to claim the money by logging into his account or registering a new account. After all, he already had an account with the service. It turned out, the coworker had accidentally forgotten to include dots with his email address. So, there was indeed no PayPal account for that exact email address.
This is not an uncommon situation. Google ignores dots in email addresses and offers gmail.com as shorthand spelling for googlemail.com. Emails sent to john.doe@gmail.com will be forwarded to the same inbox as emails to johndoe@googlemail.com. PayPal allows their users to add several addresses to the same account to accommodate such practices. And after logging in with the existing account and adding the alternative email address to that account, my friend was able to claim the money.
The one thing that remained confusing: he also received an email stating that the withdrawal limit for his account had been removed. Now, whether that was caused by his own doing or not, was the main cause for alarm. He ended all active login sessions and changed the password for good measure. In the end, no money was lost or stolen.
All’s Well That Ends Well?
Well, almost. Or kind of. The money arrived in the account it was meant to and the right person got access to it. But, a similar situation could be exploited by attackers using well-known (and still largely successful) social engineering tactics.
- Establishing the occasion and the context of the transfer – social information is readily available on the internet, including birthdays and work anniversaries. It is very easy for attackers to make use of this information and construct a believable scenario in which a victim receives a PayPal transaction like the one above.
- Getting people to click an email link – It is convenient that PayPal routinely sends emails out with instructions to claim money by logging in or registering. It is also convenient that Google forwards emails with or without dots to the same inbox. So, an attacker might assume that a victim has not yet linked all alternate Google email addresses with their email account and craft an email with a phishing link. Given the well-constructed context of the situation, victims might be more inclined to click the link.
- Gaining access to the victim’s account – Stealing a victim’s credentials may seem like the hardest bit for an attacker, but it might not be. People are notoriously bad at reading URLs or forget to check the URL before they click altogether. Tools are available that facilitate credential stealing (including stealing Multi-Factor-Authentication credentials). A good example is EvilProxy, which fakes login pages and has gained popularity for its quality and ease of use.
Once an attacker gets access to a PayPal account, they can trigger transfers. PayPal’s protective measures might prevent the worst, but you will likely find yourself short of some money.
An attacker might also like to harvest your credentials for later use or to sell them. That is particularly easy if you are not using MFA – otherwise the attacker would likely lose access once your session expired.
What Should You Do To Protect Yourself?
This kind of exploit has not been successful to my knowledge, and there are a number of things people can do to protect themselves.
- Double-check the legitimacy of any transaction using a different channel – in this case, the transaction was expected and legitimate. If something appears odd, checking with the sender is the first thing you should do.
- Do not click on links in emails and subsequently log into pages unless you are absolutely sure the page you are using is PayPal’s legitimate business page. Better: type the URL yourself into the browser bar.
- Use MFA with PayPal – really, there is no reason not to.
- Be vigilant and remain wary of calls to action – particularly if these calls invoke a sense of greed, curiosity, the promotion of self-interest, urgency, fear or helplessness.
With thanks to Martin Kraemer at KnowBe4.
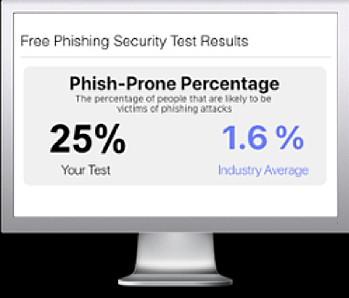
Free Phishing Security Test
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Here’s how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/phishing-security-test-partner?partnerid=001a000001lWEoJAAW

