Beware of Spoofed Vanity URLs

Researchers at Varonis warn that attackers are using customizable URLs (also known as vanity URLS) on SaaS services to craft more convincing phishing links. The attackers have used this technique for links created through Box, Zoom, and Google Docs and Forms.
“While vanity URLs provide a custom, easy-to-remember link, Varonis Threat Labs discovered that some applications do not validate the legitimacy of the vanity URL’s subdomain (e.g., yourcompany.example[.]com), but instead only validate the URI (e.g., /s/1234),” the researchers write. “As a result, threat actors can use their own SaaS accounts to generate links to malicious content (files, folders, landing pages, forms, etc.) that appears to be hosted by your company’s sanctioned SaaS account. Achieving this is as easy as changing the subdomain in the link. These spoofed URLs can be used for phishing campaigns, social engineering attacks, reputation attacks, and malware distribution.”
The researchers explain that this technique can fool security technologies as well as humans.
“A document, image, or binary file has a much higher probability of successfully infecting a user or tricking them into entering sensitive information when hosted on their own company’s ‘official’ Box account versus being distributed through a generic file-sharing URL the user doesn’t recognize,” the researchers write. “If their company has sanctioned Box usage in the organization, web filters and cloud access security brokers won’t be able to block this phishing link. For increased deception, the attacker can also add password protection to the file to make it seem safer to the victim, or upload a custom logo and modify the color scheme in their malicious Box account to match the look and feel of the company they’re spoofing.”
Varonis says users should be wary when they click on third-party links, even if the URL has the name of their organization in it.
“Users may get a warning message when visiting a spoofed Zoom URL,” the researchers write. “However, since users often click through non-critical warning messages, Varonis Threat Labs recommends being cautious when accessing branded Zoom links and avoid entering sensitive personal information into meeting registration forms, even if the form appears to be hosted by your company on an official subdomain with the correct logo and branding.”
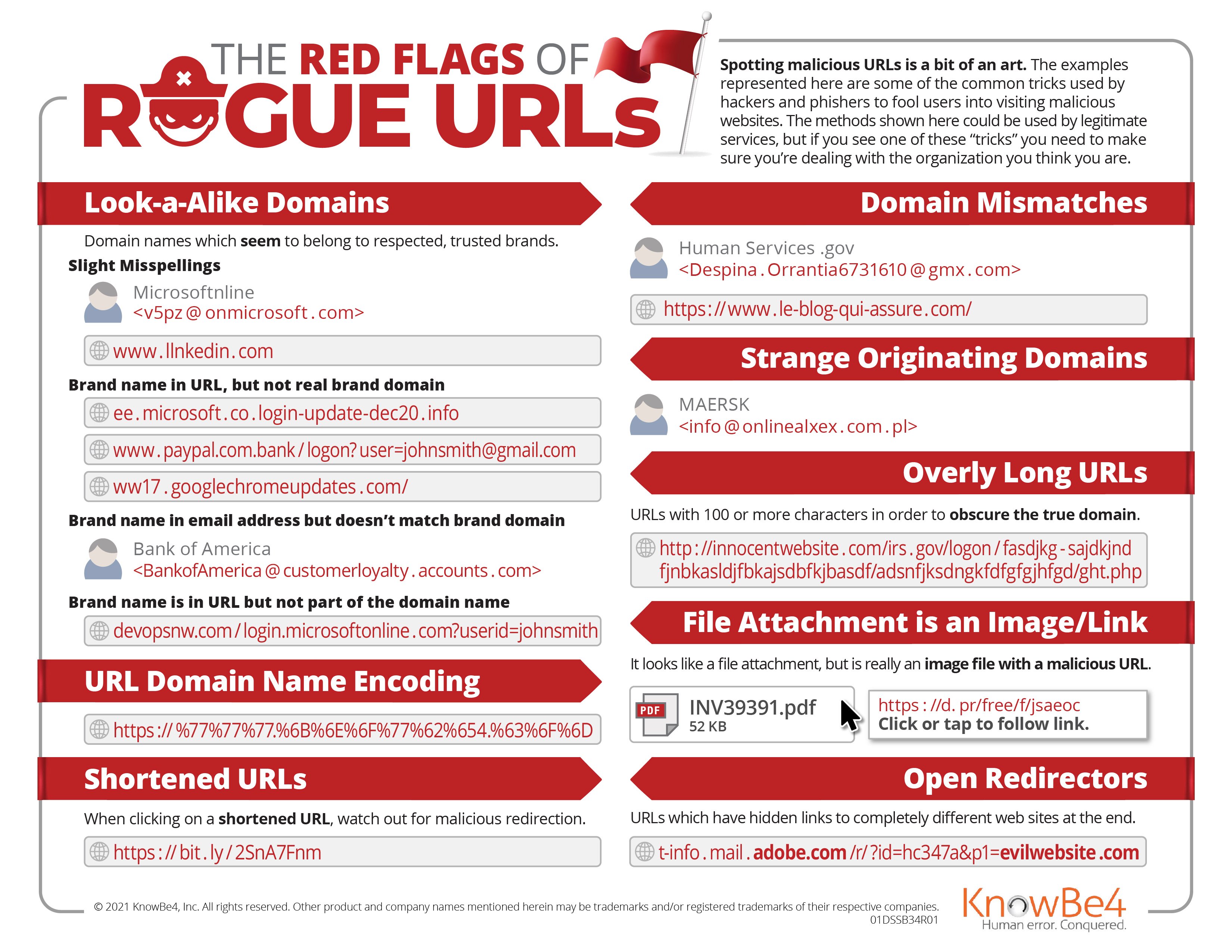
New-school security awareness training can teach your employees how to recognize social engineering attacks so they can thwart phishing attacks. Our infographic “The Red Flags of Rogue URLs” shows what to watch out for in attacks like these.
The world’s largest library of security awareness training content is now just a click away!
In your fight against phishing and social engineering you can now deploy the best-in-class simulated phishing platform combined with the world’s largest library of security awareness training content; including 1000+ interactive modules, videos, games, posters and newsletters.
You can now get access to our new ModStore Preview Portal to see our full library of security awareness content; you can browse, search by title, category, language or content topics.

The ModStore Preview includes:
- Interactive training modules
- Videos
- Trivia Games
- Posters and Artwork
- Newsletters and more!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/security-awareness-training-preview-partner?partnerid=001a000001lWEoJAAW

