Callback phishing attacks see massive 625% growth since Q1 2021

Hackers are increasingly moving towards hybrid forms of phishing attacks that combine email and voice social engineering calls as a way to breach corporate networks for ransomware and data extortion attacks.
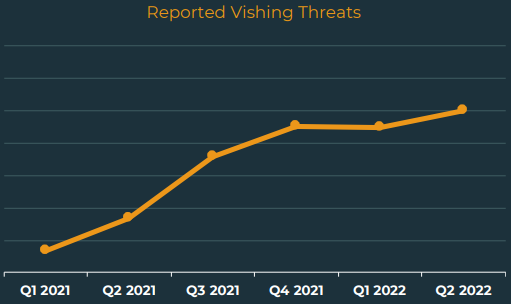
According to Agari’s Q2 2022 cyber-intelligence report, phishing volumes have only increased by 6% compared to Q1 2022. However, the use of ‘hybrid vishing’ is seeing a massive 625% growth.
Vishing, “voice phishing,” involves some form of a phone call to perform social engineering on the victim. Its hybrid form, called “callback phishing,” also includes an email before the call, typically presenting the victim with a fake subscription/invoice notice. The recipient is advised to call on the provided phone number to resolve any issues with the charge, but instead of a real customer support agent, the call is answered by phishing actors.
The scammers then offer to resolve the presented problem by tricking the victim into disclosing sensitive information or installing remote desktop tools on their system. The threat actors then connect to the victim’s device remotely to install further backdoors or spread to other machines.
These callback phishing attacks were first introduced by the ‘BazarCall/BazaCall’ campaigns that appeared in March 2021 to gain initial access to corporate networks for ransomware attacks.
The attacks work so well that multiple ransomware and extortion gangs, such as Quantum, Zeon, and Silent Ransom Group, have adopted the same technique today to gain initial network access through an unsuspecting employee.
“Hybrid Vishing attacks reached a six-quarter high in Q2, increasing 625% from Q1 2021. This threat type also contributed to 24.6% of the overall share of Response-Based threats,” details the Agari report. “While this is the second quarter hybrid vishing attacks have declined in share due to the overall increase of response-based threats, vishing volume has steadily increased in count over the course of the year.”
New-school security awareness training can enable your employees to thwart targeted social engineering attacks. With thanks to the Cyber Defence Alliance and BleepingComputer. The full story is here: https://www.bleepingcomputer.com/news/security/callback-phishing-attacks-see-massive-625-percent-growth-since-q1-2021/
Request A Demo: Security Awareness Training
New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn’t a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4’s security awareness training and simulated phishing platform and see how easy it can be!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/one-on-one-demo-partners?partnerid=001a000001lWEoJAAW

