Emails Are Responsible for 88% of Malicious File Deliveries

Emails are still the most common delivery method for malicious files, according to Check Point’s Cyber Security Report for 2024.
“Email-based attacks continue to be the dominant initial infection vector,” the report says.
“Eighty-eight percent of all malicious file deliveries occur through email, with the remainder downloaded directly from the internet. Threat actors have adapted to email protection strategies and are exploring innovative delivery techniques. Following Microsoft’s restrictions on Office VBA macros in files from external sources denoted with the Mark-of-the-Web (MotW), there was a sharp decrease in the prevalence of malicious Office files, from nearly 50% in 2022 to 2% in 2023. Notable alternative attack vectors include HTML files and various archive file types.”
Notably, the researchers observed a spike in the use of HTML files to deliver malicious content.
“In particular, the exploitation of HTML files saw a significant uptick,” the researchers write. “HTML files comprise 69% of all malicious file attachments. Threat actors use HTML files in several ways. They are used in phishing schemes to imitate legitimate website login pages and steal user credentials. They can include malicious JavaScripts or exploits to unpatched browser and browser-plugins. As demonstrated in recent CP<R> research, these tactics are not limited to low-level criminals but are also utilized by advanced APT actors. Other uses of HTML include HTML smuggling, or auto download for executables and redirections to other malicious URLs. Legitimate use cases of email-delivered HTML are unusual and therefore organizations should consider implementing restrictions.”
Attackers are also using password-protected archives to avoid detection by security filters.
“Utilization of various archive files has also been on the rise,” Check Point says. “The contents of password-protected archives are hidden from many security services, thus forming an effective attack vector. Other formats like .img and .iso depend on the software used for their extraction to propagate the MotW functionality, which is used to prevent malicious attempts. While Microsoft has fixed this feature, other providers like 7-zip have opt-in policies, thus decreasing the effectiveness of the MotW protection mechanism.”
KnowBe4 empowers your workforce to make smarter security decisions every day. Over 65,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.
Check Point has the story.
Free Phishing Security Test
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
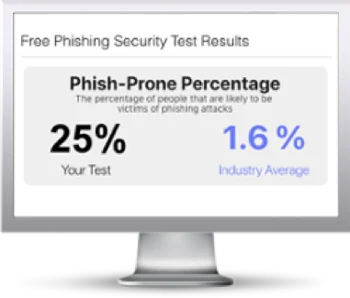
Here’s how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/phishing-security-test-partner?partnerid=001a000001lWEoJAAW

