Latest QBot Attacks Use a Mixture of PDF Attachments and Windows Scripting Host Files to Infect Victims

QBot malware seems to be outliving its competitors through innovative new ways to socially engineer victims into helping install it.
Because “good guys” are constantly updating the way they detect attacks, cybercriminals need to run at an equally fast pace, coming up with new ways to see malware installed on victim endpoints. What determines the longevity of a piece of malware really comes down to whether its authors are working to stay ahead of security solutions.
This appears to be the case with Qbot. Since 2008, we’ve seen QBot in the past using a wide variety of tactics, including HTML Smuggling, and it continues to be a formidable foe, with its latest iteration using several tactics together.
First, it uses an HTML attachment made to appear as if it’s a PDF file. The HTML downloads and opens a PDF that asks the user to click the “OPEN” button to reveal the “protected file.”
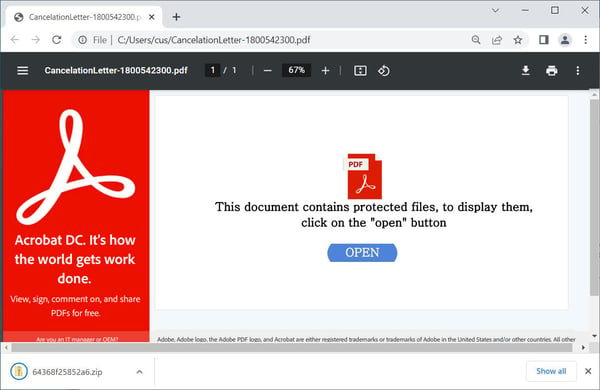
This user interaction is the key. The clicking of the button causes a ZIP file that contains a Windows scripting host file (WSF file) to launch. The ZIP file helps obfuscate the malicious intent of the scripting file from security solutions.
The script installs QBot onto the endpoint.
As I mentioned, the interaction by the user is the key – to this and every phishing attack other than response-based attacks (where the attacks are purely social engineering). By training users through security awareness training to not interact with emails they are unsure of, organizations can significantly reduce the risk of a successful cyber attack.
BleepingComputer has the story.
The world’s largest library of security awareness training content is now just a click away!
In your fight against phishing and social engineering you can now deploy the best-in-class simulated phishing platform combined with the world’s largest library of security awareness training content; including 1000+ interactive modules, videos, games, posters and newsletters.
You can now get access to our new ModStore Preview Portal to see our full library of security awareness content; you can browse, search by title, category, language or content topics.
The ModStore Preview includes:
- Interactive training modules
- Videos
- Trivia Games
- Posters and Artwork
- Newsletters and more!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/one-on-one-demo-partners?partnerid=001a000001lWEoJAAW

