Malware campaign impersonates VC firm looking to buy sites
BleepingComputer was recently contacted by an alleged “venture capitalist” firm that wanted to invest or purchase our site. However, as we later discovered, this was a malicious campaign designed to install malware that provides remote access to our devices.
Last week, BleepingComputer received an email to our contact form from an IP address belonging to a United Kingdom virtual server company.
This email pretended to be from a venture capitalist interested in investing or buying BleepingComputer, with the whole email listed below.
“Hello, we are a group of venture capitalists investing in promising projects.
We saw your website and were astounded by your product. We want to discuss the opportunity to invest or buy a part of the share in your project. Please get in touch with us by phone or in Vuxner chat.
Your agent is Philip Bennett. His username in Vuxner is philipbennett Make sure you contact us ASAP because we are not usually so generous with our offers. Thank you in advance!”
Google showed only a few results for ‘Vuxner,’ with one being for a well-designed and legitimate-looking vuxner[.]com, a site promoting “Vuxner Chat – Next level of privacy with free instant messaging.” As this appeared to be the “Vuxner chat” the threat actors referenced in their email, BleepingComputer attempted to download it and run it on a virtual machine. BleepingComputer found that the VuxnerChat.exe download [VirusTotal] actually installs the “Trillian” messaging app and then downloads further malware onto the computer after Trillian finishes installing.
As you can see, threat actors are willing to create elaborate campaigns consisting of fake sites, custom installers, and targeted emails to infect their victims. For this reason, all business owners and consumers need to be wary of any unusual emails stating that you need to download something to communicate with them.
Receiving emails like the one BleepingComputer received should automatically be seen as suspicious, and recipients should research to determine if a particular software is legitimate or not. Simply searching and seeing a single result related to a particular program is a huge red flag indicating that the program should be avoided.
With thanks to the Cyber Defence Alliance and BleepingComputer. The full story is here: https://www.bleepingcomputer.com/news/security/malware-campaign-impersonates-vc-firm-looking-to-buy-sites/
Find out which of your users’ emails are exposed before bad actors do.
Many of the email addresses and identities of your organization are exposed on the internet and easy to find for cybercriminals. With that email attack surface, they can launch social engineering, spear phishing and ransomware attacks on your organization. KnowBe4’s Email Exposure Check Pro (EEC) identifies the at-risk users in your organization by crawling business social media information and now thousands of breach databases.
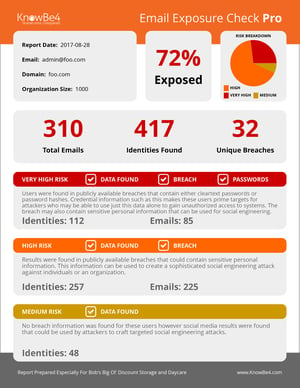
Here’s how it works:
- The first stage does deep web searches to find any publicly available organizational data
- The second stage finds any users that have had their account information exposed in any of several thousand breaches
- You will get a summary report PDF as well as a link to the full detailed report
- Results in minutes!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/email-exposure-check-pro-partner?partnerid=001a000001lWEoJAAW


