Microsoft Warns of Signed Drivers Being Used to Terminate AV and EDR Processes

The malicious abuse of several developer program accounts in Microsoft’s Windows Hardware Developer Program allowed threat actors to have malware evade detection.
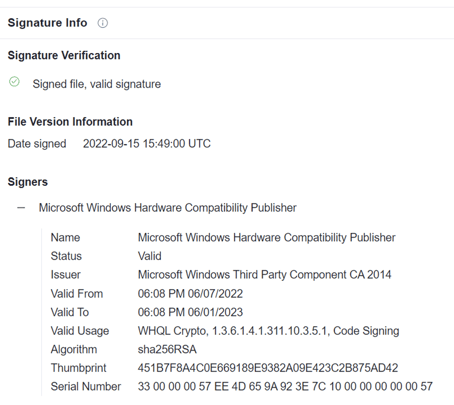
It’s a long-term play, but one that is quite an impressive feat – threat actors sought to compromise credentials that gave them access to submit malware-embedded drivers for Microsoft certification – something that would cause security products to see them as trustworthy and allow them to run. The signature below shows how very valid these drivers appear to an attacked system – there isn’t a hint that anything is afoot when you look at it:
According to security vendor SentinelOne, the drivers contained POORTRY and STONESTOP malware, part of a small toolkit designed to terminate antivirus and EDR processes. Security vendor Mandiant observed a threat group designated only as UNC3944 using SMS phishing as the initial attack vector to obtain credentials that would later be used to gain access to systems to deploy the signed driver.
The use of a driver is a brilliant touch, but threat actors still need to gain access to systems – which means obtaining credentials, a method of entry, etc. Usually this involves some interaction with a user (via texting, in the case of Mandiant’s research). And while it’s possible to see these kinds of driver-based efforts begin with vulnerabilities, it’s necessary for organizations to ensure any email- or web-based initial access is relegated to an absolute minimum – something accomplished by enrolling users in ongoing Security Awareness Training to ensure they see malicious content for what it really is.
The world’s largest library of security awareness training content is now just a click away!
In your fight against phishing and social engineering you can now deploy the best-in-class simulated phishing platform combined with the world’s largest library of security awareness training content; including 1000+ interactive modules, videos, games, posters and newsletters.
You can now get access to our new ModStore Preview Portal to see our full library of security awareness content; you can browse, search by title, category, language or content topics.

The ModStore Preview includes:
- Interactive training modules
- Videos
- Trivia Games
- Posters and Artwork
- Newsletters and more!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/security-awareness-training-preview-partner?partnerid=001a000001lWEoJAAW

