New Credential Harvesting Scam Impersonates Google Translate to Trick Victims

In an interesting twist, this latest scam identified by security researchers at Avanan attempts to establish legitimacy by making the victim think the logon page is being translated.
Most scams focused on stealing the victim’s credentials tend to spoof the specific platform to which the credentials provide access. We’ve seen it time and time again with attacks on Microsoft 365 users. But in this latest attack – apparently on G Suite users – the threat actors got somewhat creative.
The initial phishing email targets Spanish-speaking users, using a pretty common social engineering tactic revolving around the need to confirm an account.
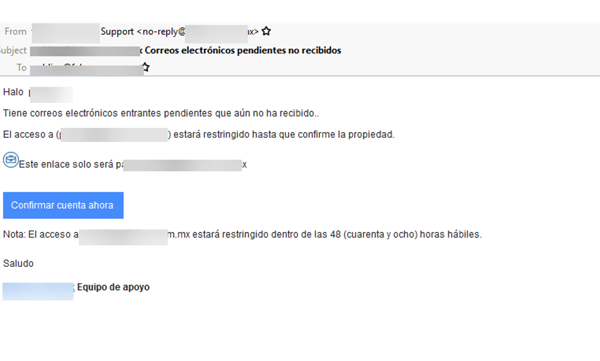
Source: Avanan
The unique execution here is the spoofing of a Google Translate page to make the victim user believe they are providing credentials within a safe environment – one owned and operated by Google.
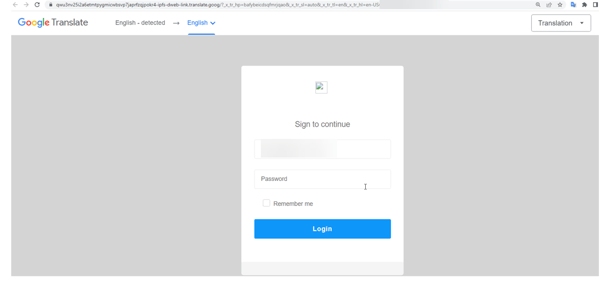
Source: Avanan
This additional step helps to establishing the illusion of legitimacy for the victim, lowering the defenses and increasing the chances they will provide their credentials.
There are telltale signs that this email is totally bogus: the sender’s email address and the URL on the “Google Translate” page both don’t match up – something easily spotted by users that undergo continual Security Awareness Training.
Can hackers spoof an email address of your own domain?

Are you aware that one of the first things hackers try is to see if they can spoof the email address of your CEO? If they are able to commit “CEO Fraud”, penetrating your network is like taking candy from a baby.
Now they can launch a “CEO fraud” spear phishing attack on your organization, and that type of attack is very hard to defend against, unless your users are highly ‘security awareness’ trained.
Find out now if your domain can be spoofed. The Domain Spoof Test (DST) is a one-time free service. Run this test so you can address any mail server configuration issues that are found.
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/domain-spoof-test-partner?partnerid=001a000001lWEoJAAW

