“Operation Kaerb” Takes Down Sophisticated Phishing-as-a-Service Platform “iServer”

A partnering of European and Latin American law enforcement agencies took down the group behind the mobile phone credential theft of 483,000 victims.
Someone steals a physical mobile phone and they need to unlock it. But to do so, you need the Apple ID or Google account of the phone’s owner. So, where do you go? Well, it used to be iServer – an automated phishing-as-a-service platform that could harvest credentials to unlock the stolen phones.
According to security vendor Group-IB, who participated in Operation Kaerb, iServer used a web interface to help “low-skilled criminals, known as ‘unlockers” to steal device details passwords, user credentials from cloud-based mobile platforms and other personal information from victims through text messages like the one below:

Source: Group-IB
The intent was to provide the unlocker with enough details to allow them to bypass “Lost Mode” and unlock the stolen phone.
In a recent press release, Group IB announced the successful arrest of 17 individuals across Latin America and in Spain last month, putting a 5-year run to an end.
The very existence of such a platform demonstrates how cunning cybercriminals can be in creating solutions that meet a malicious need – such as unlocking a stolen phone. The phishing attacks rely on social engineering and a less-than-vigilant phone owner. Through proper security awareness training individuals can be taught to maintain that sense of vigilance – even after a traumatic event like having your phone stolen.
KnowBe4 empowers your workforce to make smarter security decisions every day. Over 70,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.
Free Phishing Security Test
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
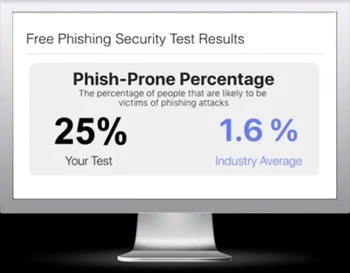
Here’s how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry

