Over Half of all Impersonation Attacks Target Non-Executive Employees

A new report shows how cybercriminals focus on users that are less vigilant and more prone to falling for social engineering and impersonation tactics designed to gain access to finances.
Threat actors have plenty of viable data on who to target, what roles fall victim to attacks, who ignores attack attempts, etc. So, while they want to hit someone with a lot of responsibility – say, the CFO, they most likely have internal statistics on what level of employee is the best to target.
According to the 2021 1H Cyber Report from Avanan, 29.4% of impersonation emails target the C-Suite. But, because it’s likely IT and Security teams are focused on protecting those roles more diligently than a lower-level employee, cybercriminals have changed their tactics. Avanan’s research indicates that 51.9% of impersonation attacks target non-executives. In one example of social engineering provided in the report, an employee is targeted strictly to establish credibility by the sender as a legitimate employee by first requesting a Direct Deposit form:
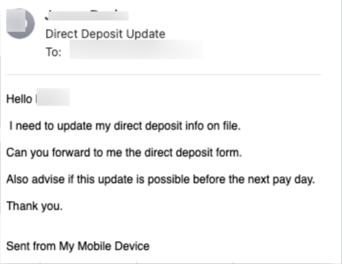 Source: Avanan
Source: Avanan
This builds trust between the target employee (likely in Finance) and the attacker. Follow-up attacks can involve more social engineering, malicious links, attempts at banking fraud, and more.
This level of impersonation and social engineering usually involves no malicious attachments, making detection via security solutions difficult, and demands that organizations address the security vulnerability that exists – the target user. By putting all employees that have access to personal data, financials, and any other piece of valuable information through continual Security Awareness Training your prepare them for these kinds of social engineering attacks, making even the lowest employee in the ranks a part of your defense strategy.
Will your users respond to phishing emails?
KnowBe4’s new Phishing Reply Test (PRT) is a complimentary IT security tool that makes it easy for you to check to see if key users in your organization will reply to a highly targeted phishing attack without clicking on a link. PRT will give you quick insights into how many users will take the bait so you can take action to train your users and better protect your organization from these fraudulent attacks!

Here’s how it works:
- Immediately start your test with your choice of three phishing email reply scenarios
- Spoof a Sender’s name and email address your users know and trust
- Phishes for user replies and returns the results to you within minutes
- Get a PDF emailed to you within 24 hours with the percentage of users that replied
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/phishing-reply-test-partner?partnerid=001a000001lWEoJAAW

