Phishing Attacks Are Increasingly Targeting Social Media and Smartphone Users

Threat actors are increasingly tailoring their attacks to target social media apps and smartphone users, according to a new report from the Anti-Phishing Working Group (APWG).
As email security technologies improve, scammers are turning to social media apps, text messages, and voice calls to conduct social engineering attacks.
Matthew Harris, Senior Product Manager, Fraud at OpSec, explained, “We have observed an increased share of fraud being targeted towards sites that do not require high security, such as social media sites like Facebook and LinkedIn, and SAAS and Webmail accounts such as Microsoft Outlook and Netflix.”
The report also found that the volume of phishing attacks targeting bank accounts has fallen compared to last year, but these attacks have grown more sophisticated and targeted. Attackers need to put more effort into banking-focused attacks since these institutions typically have additional layers of security.
“Banks require two-factor authentication for online banking, such as codes sent to the users’ mobile phones,” the report says. “Without those authentication codes, phishers can’t get into victims’ online financial accounts. So instead, fraudsters are using phone-based methods to phish bank and payment service users. These are more immediate contact methods, and allow the fraudster to talk victims out of their sensitive information.
Phone-based fraud is initiated by different methods. One is voice phishing or vishing — where fraudsters call potential victims. Another is SMS-based phishing or smishing – in which fraudsters advertise the URLs of phishing sites within SMS (Short Message Service) and Internet-generated, phone-to-phone text messages.”
The majority of scams in Q2 2024 involved gift card fraud or advance fee requests. APWG contributor Fortra found that the average amount of money requested in business email compromise (BEC) attacks rose by 6.5% last quarter to reach $89,520.
KnowBe4 empowers your workforce to make smarter security decisions every day. Over 70,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.
The APWG has the story.
Find out which of your users’ emails are exposed before bad actors do.
Many of the email addresses and identities of your organization are exposed on the internet and easy to find for cybercriminals. With that email attack surface, they can launch social engineering, spear phishing and ransomware attacks on your organization. KnowBe4’s Email Exposure Check Pro (EEC) identifies the at-risk users in your organization by crawling business social media information and now thousands of breach databases.
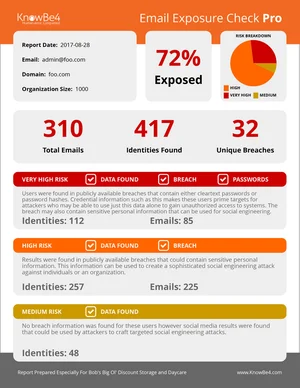
Here’s how it works:
- The first stage does deep web searches to find any publicly available organizational data
- The second stage finds any users that have had their account information exposed in any of several thousand breaches
- You will get a summary report PDF as well as a link to the full detailed report
- Results in minutes!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser:https://info.knowbe4.com/email-exposure-check-pro-partner?partnerid=001a000001lWEoJAAW

