Phishing emails deliver spooky zombie-themed MirCop ransomware
A new phishing campaign pretending to be supply lists infects users with the MirCop ransomware that encrypts a target system in under fifteen minutes.
The actors begin the attack by sending an unsolicited email to the victim, supposedly following up on a previous arrangement about an order.
The email body contains a hyperlink to a Google Drive URL, which, if clicked, downloads an MHT file (webpage archive) onto the victim’s machine.
Google Drive serves to introduce legitimacy to the email and aligns very well with common day-to-day business practices.
For threat actors, simple but key choices like this can distinguish between the victim clicking the URL or sending the email to the spam folder.
Those who open the file can only see a blurred image of what is supposedly a supplier list, stamped and signed for an extra touch of legitimacy.
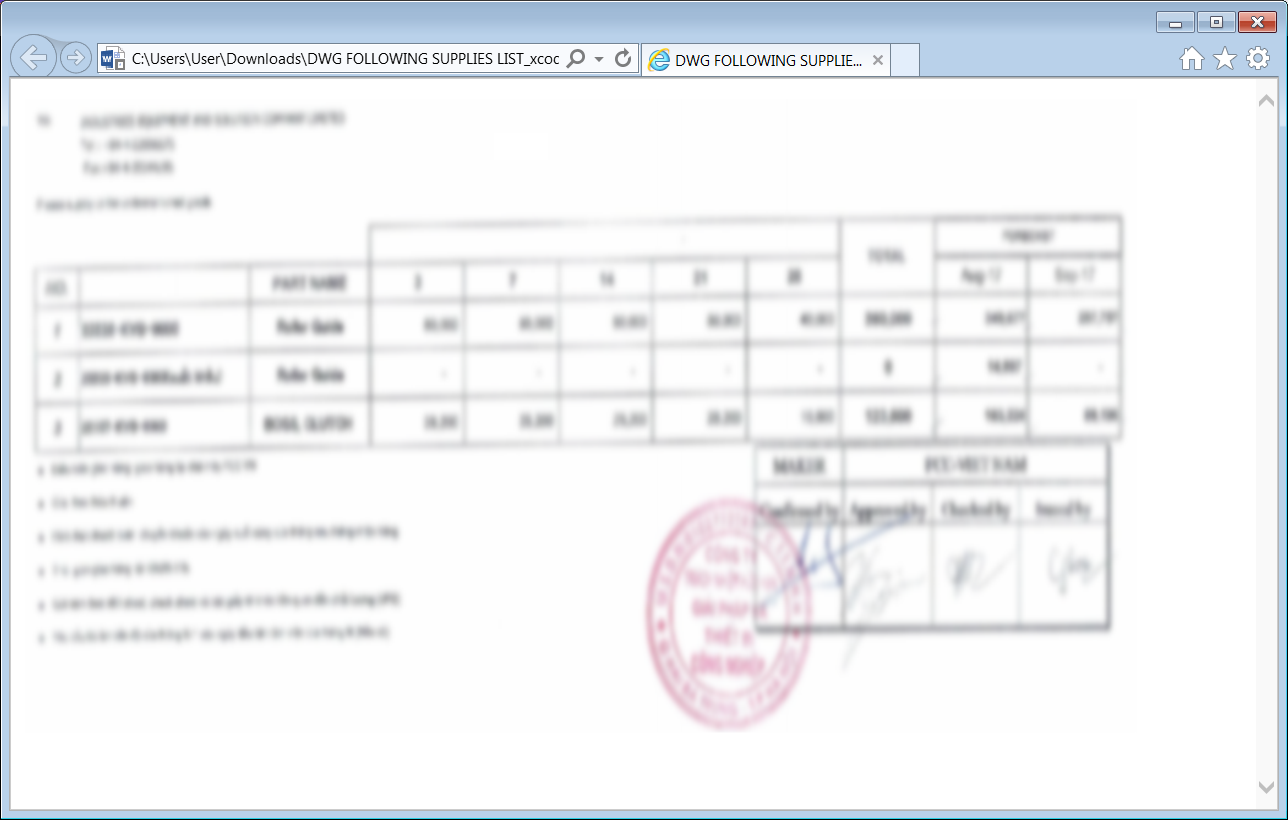
When the MHT file iis opened, it will download a RAR archive containing a .NET malware downloader from “hXXps://a[.]pomf[.]cat/gectpe.rar”.
The RAR archive contains an EXE file, which uses VBS scripts to drop and execute the MirCop payload onto the infected system.
The ransomware activates immediately and starts taking screenshots, locks files, changes the background to a horrid zombie-themed image, and offers victims instructions on what to do next.
According to Cofense, this whole process takes less than 15 minutes from the moment the victim opens the phishing email.
After that, the user is only allowed to open specific web browsers to communicate with the actors and arrange the payment of the ransom.
The actors are not interested in sneaking into the victim’s machine stealthily or staying there for long to conduct cyber-espionage or steal files for extortion.
On the contrary, the attack unfolds rapidly, and the source of trouble becomes quickly evident to the victim.
Security Awareness Training is the means by which organizations teach users how to stay in that ever-vigilant mode when interacting with email and the web. By doing so, instead of taking everything at face value and believe it by default, users interact with unfamiliar content like this in a far-more scrutinizing manner and are less likely to become victims.
With thanks to the Cyber Defence Alliance and Bleeping Computer. The full story is here: https://www.bleepingcomputer.com/news/security/phishing-emails-deliver-spooky-zombie-themed-mircop-ransomware/
Free Phish Alert Button
Do your users know what to do when they receive a phishing email? KnowBe4’s Phish Alert Button gives your users a safe way to forward email threats to the security team for analysis and deletes the email from the user’s inbox to prevent future exposure. All with just one click! Phish Alert benefits:
Here’s how it works:
- Reinforces your organization’s security culture
- Users can report suspicious emails with just one click
- Incident Response gets early phishing alerts from users, creating a network of “sensors”
- Email is deleted from the user’s inbox to prevent future exposure
- Easy deployment via MSI file for Outlook, G Suite deployment for Gmail (Chrome)
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/free-phish-alert-partner?partnerid=001a000001lWEoJAAWEdit This Most Recent Posts


