Phishing for Love: A Sharp Surge in Valentine’s Day-Themed Scams

If a recipient does not have an anti-phishing tool to identify and block the link, clicking it would trigger a Captcha, as shown in the screenshot below. Normally used to verify that a user is human rather than an automated bot, Captchas in these types of attacks are employed to block certain forms of link scanning functionality, including end-destination scanning, preventing security tools from detecting malicious sites.
From there, the malicious site could be used to harvest the recipient’s credentials, download malware onto their device, and potentially steal sensitive information or gain unauthorized access to personal or organizational accounts.
Screenshot of the captcha that appears if the malicious link was clicked
Example 2 – Combining Seasonal Events
Cybercriminals have taken it a step further over Super Bowl Weekend (February 9-8th), leveraging the excitement of a major cultural event alongside Valentine’s Day to create a double threat, targeting victims with highly relevant and timely scams.
In this example, the attackers have impersonated the NFL. However, the template is less sophisticated than the first, using a mix of images, links, and text within the body. The message urges the recipient to click a link to claim a free gift, once again employing social engineering tactics like time limits to create a sense of urgency.
Screenshot of a phishing attack that impersonates the NFL, with KnowBe4 anti-phishing banners applied.
Mitigating Advanced Threats with Human Risk Management
In 2024, we saw a 43% increase in attacks impersonating dating apps, highlighting that cybercriminals have recognized the effectiveness of exploiting this holiday season—tapping into heightened emotions and people’s desire for a good deal.
These attacks are strategically timed to align with an increase in legitimate emails about holidays and key events, maximizing their chances of success. It’s no surprise, then, that we’ve seen a 34.81% increase in Valentine’s Day-themed scams this year. Cybercriminals only pursue attacks that deliver a return, and clearly, these tactics are paying off.
To effectively combat these threats, it’s crucial to pair timely user education and coaching with intelligent anti-phishing solutions. While educating users on the dangers of phishing and how to spot suspicious messages is essential, advanced technological defenses, such as machine learning and AI-powered detection, play a critical role in identifying and neutralizing these threats. Together, these strategies form a comprehensive defense that can better protect individuals and organizations from sophisticated phishing attacks.
So this Valentine’s Day, love may have been in the air, but so were cyber threats. As we celebrated the season of love, we had to remember that cybercriminals were also targeting our hearts—and our personal data. While Valentine’s Day has passed, the need to stay alert and cautious when clicking on links or sharing sensitive information remains important all year round.
RanSim
Free downloadable software tool
Threat actors are constantly coming out with new strains to evade detection. Is your network effective in blocking all of them when employees fall for social engineering attacks?
RanSim gives you a quick look at the effectiveness of your existing network protection. RanSim will test 24 ransomware infection scenarios and 1 cryptomining infection scenario and show you if a workstation is vulnerable.
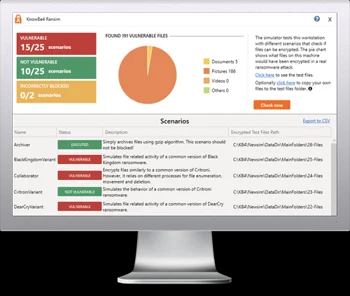
Here’s how it works:
- 100% harmless simulation of real ransomware and cryptomining infections
- Does not use any of your own files
- Tests 25 types of infection scenarios
- Just download the installer and run it
- Results in a few minutes!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/ransomware-simulator-tool-partner?partnerid=001a000001lWEoJAAW

