Phishing Kit Imitates PayPal

Researchers at Akamai have discovered a PayPal phishing kit that attempts to steal victims’ identities as well as their financial information. The phishing page looks identical to Paypal’s login page, and asks users to solve a captcha before entering their username and password. The researchers note that asking for the captcha can instill a sense of trust in the user, since they feel like the site is asking for security measures.
After the victim has apparently logged in, the site tells them that suspicious activity has been detected on their account and asks them to verify their payment card information. In addition, the site asks for the user’s social security number, mother’s maiden name, and their card’s PIN. After this, the site asks the user to take a picture of themselves holding their passport, driver’s license, or national ID. Akamai notes that this is “well beyond what a typical phishing kit would attempt to gather,” and could be used to create cryptocurrency accounts using the victim’s identity.
The phishing kit also avoids IP addresses that are known to belong to various security companies, in order to avoid being flagged as malicious.
“One of the unique aspects of this phishing kit is its attempt to evade detection by cross-referencing IP addresses to specific domains,” the researchers write. “It provides multiple different checks on the connecting IP address to ensure that it doesn’t match specific domains or originate from security organizations. It does this by comparing the connecting IP address with a list of static IP ranges and domains it has hard-coded in its source files. These IP ranges are the network blocks of companies like Google, Microsoft, Sucuri, etc. It also checks the IP address against an IP reputation site using an API key that is embedded in the code, looking for any IPs that may be flagged as malicious.”
New-school security awareness training can enable your employees to thwart phishing and other social engineering attacks.
Akamai has the story.
Free Phishing Security Test
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
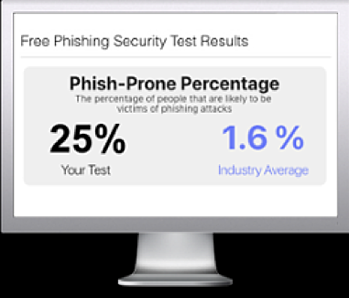
Here’s how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/phishing-security-test-partner?partnerid=001a000001lWEoJAAW

