Piggybacking: Social Engineering for Physical Access

Tailgating or piggybacking is an old but effective social engineering technique to gain physical access to restricted areas, according to Rahul Awati at TechTarget. Tailgating is when a bad actor simply follows an employee through a door that requires authentication.
“Tailgating is one of the simplest forms of a social engineering attack,” Awati writes. “It is an easy way for an unauthorized party to get around security mechanisms that are assumed to be secure. The security comes into question due to a combination of human carelessness (the followed party) and ingenuity (the following party). For example, a retina scanner is meant to limit entry to a physical area by scanning the retinas of authorized personnel. While retina scanning authentication works, unauthorized parties can gain access to a secured area if an employee holds the door for an unknown person behind them out of a misguided sense of courtesy or habit. Such a polite gesture may be exploited by individuals to gain access to a location they might not have been able to access otherwise.”
Tailgating most often occurs when an employee holds the door for another person out of politeness.
“Threat actors take advantage of cognitive biases that affect human decision-making,” Awati says. “One such ‘human bug’ is the tendency to be courteous. Another is the tendency to trust other people. A person holding the door open doesn’t typically assume that a tailgating person is not supposed to be there, or worse, intends to harm the organization. Tailgating is a common problem in multi-tenanted buildings where many people access the building, making it difficult to track unauthorized personnel and keep them out. Tailgating also happens more often in companies where employees don’t follow cybersecurity best practices. This may be due to carelessness or inadequate training.”
Not that you want everyone to be rude, but all fair-minded people understand that you can’t sacrifice security for politeness. New-school security awareness training can give your employees a healthy sense of suspicion so they can thwart social engineering attacks.
TechTarget has the story.
Free Phishing Security Test
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
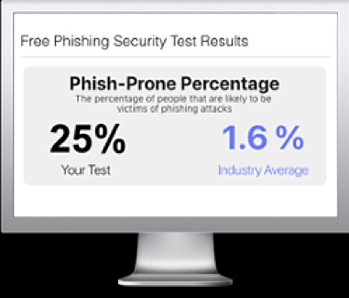
Here’s how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/phishing-security-test-partner?partnerid=001a000001lWEoJAAW

