QBot phishing uses Windows Calculator sideloading to infect devices

The operators of the QBot malware have been using the Windows Calculator to side-load the malicious payload on infected computers.
DLL side-loading is a common attack method that takes advantage of how Dynamic Link Libraries (DLLs) are handled in Windows. It consists of spoofing a legitimate DLL and placing it in a folder from where the operating system loads it instead of the legitimate one.
QBot, also known as Qakbot is a Windows malware strain that started as a banking trojan but evolved into a malware dropper, and is used by ransomware gangs in the early stages of the attack to drop Cobalt Strike beacons.
Security researcher ProxyLife recently discovered that Qakbot, has been abusing the the Windows 7 Calculator app for DLL side-loading attacks since at least July 11. The method continues to be used in malspam campaigns.
The emails used in the latest campaign carry an HTML file attachment that downloads a password-protected ZIP archive with an ISO file inside.
The password for opening the ZIP file is shown in the HTML file, and the reason for locking the archive is to evade antivirus detection.
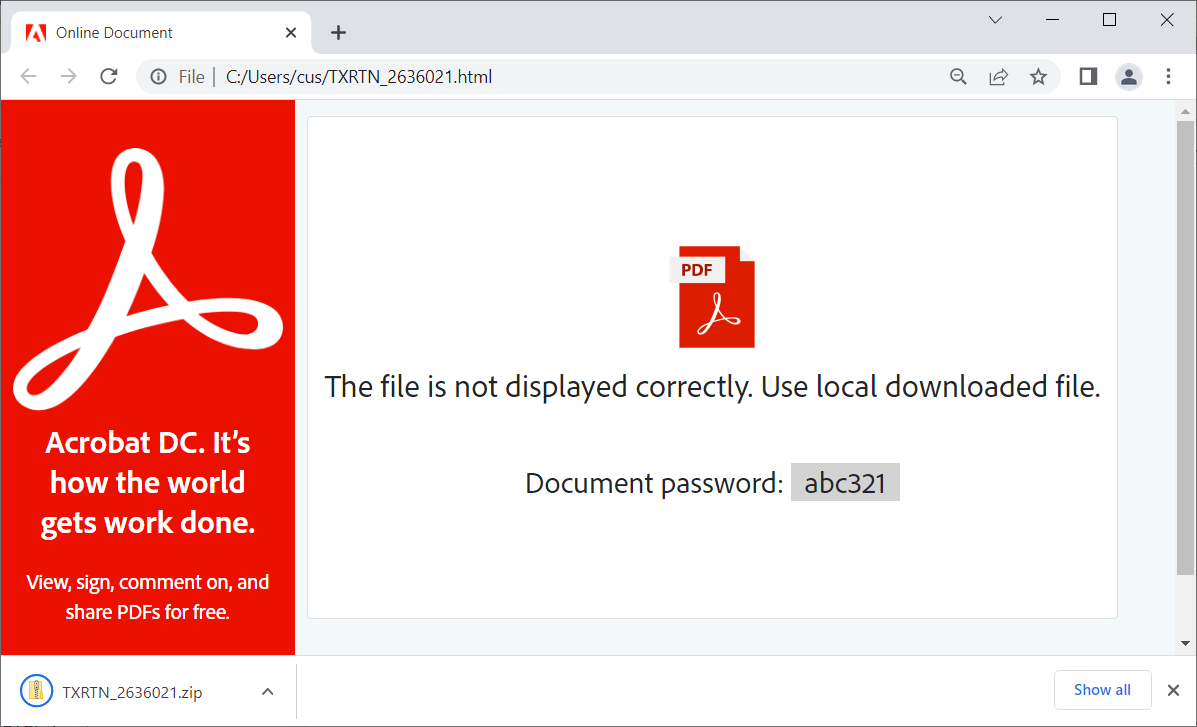
Clicking the shortcut triggers the infection by executing the Calc.exe through the Command Prompt.
When loaded, the Windows 7 Calculator automatically searches for and attempts to load the legitimate WindowsCodecs DLL file. However, it does not check for the DLL in certain hard coded paths, and will load any DLL with the same name if placed in the same folder as the Calc.exe executable.
The threat actors take advantage of this flaw by creating their own malicious WindowsCodecs.dll file that launches the other [numbered].dll file, which is the QBot malware.
By installing QBot through a trusted program like the Windows Calculator, some security software may not detect the malware when it is loaded, allowing the threat actors to evade detection.
With thanks to the Cyber Defence Alliance and BleepingComputer. The full story is here: https://www.bleepingcomputer.com/news/security/qbot-phishing-uses-windows-calculator-sideloading-to-infect-devices/
Free Ransomware Simulator Tool
Threat actors are constantly coming out with new strains to evade detection. Is your network effective in blocking all of them when employees fall for social engineering attacks?
KnowBe4’s “RanSim” gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 22 ransomware infection scenarios and 1 cryptomining infection scenario and show you if a workstation is vulnerable.
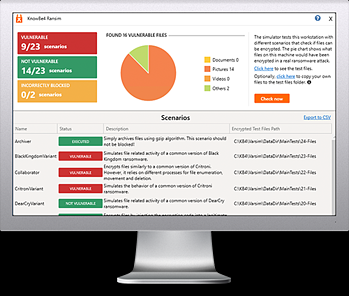
Here’s how it works:
- 100% harmless simulation of real ransomware and cryptomining infections
- Does not use any of your own files
- Tests 23 types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/ransomware-simulator-tool-partner?partnerid=001a000001lWEoJAAW

