QR-Code Attacks Target the C-Suite 42 Times More than Standard Employees

QR-code attacks leveraging QR-codes are kicking into high gear and becoming a common method used in phishing attacks, according to new data from Abnormal Security.
We saw a surge in QR-code based phishing attacks late last year. And new data in security vendor Abnormal Security’s H1 2024 Email Threat Report gives us some additional insight into how these attacks are being executed.
According to the report:
- 89.3% of QR code attacks are credential phishing
- 27% of attacks impersonate multi-factor authentication (MFA) notifications
- 21% of attacks sent targets fake notifications of a shared document
Also, SMB (specifically organizations with up to 500 employees) companies are 19 times more likely to receive a QR code phishing attack than the largest enterprises with more than 50,000 employees.
You might be thinking, “Who’s dumb enough to take their phone and scan a QR-code off of their computer?,” or “Who can scan a QR-code from an email when they’re reading the email on their mobile device?”
But threat actors have taken this into consideration in their attacks. For example, in the image below, the attackers are using a problem with multi-factor authentication.

This example gets past the first of our collective objections to this mode of attack. And for those victims that are on the device that would otherwise scan the QR code, take the following example and note the “Can’t Scan Image” button at the lower left:

And just like that, the threat actors have convinced your user to engage with the phishing attack by click or camera. It’s that ever-present vigilance that you and I both have every time we open any email. We need to instill that into regular employees via security awareness training so they realize the lunacy of receiving a QR-code in an email, and learn to ignore or verify it rather than engage with it.
KnowBe4 empowers your workforce to make smarter security decisions every day. Over 65,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.
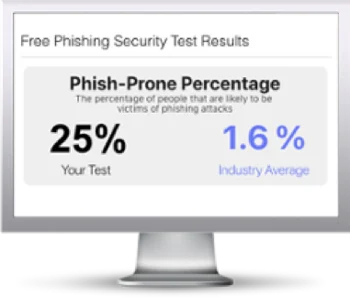
Free Phishing Security Test
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Here’s how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/phishing-security-test-partner?partnerid=001a000001lWEoJAAW

