Ransomware Attacks Surge 91% in a Single Month to Reach an All-Time High

March saw a huge jump in ransomware compared to January and February, signifying that organizations should expect to see a lot more of these attacks this year.
With security solutions getting good at spotting and stopping malware on endpoints and servers, you’d think that ransomware attacks would be dwindling. But, according to the NCC Group’s Cyber Threat Report for March 2023, it feels a lot more like 2023 is going to be a repeat of 2022, but at significantly higher attack levels.
According to the report, March of 2023 incurred 459 documented ransomware attacks. That’s a 91% rise over February of this year and a 62% increase over March of last year. Additionally, January and February both saw significant growth over their 2022 counterparts.
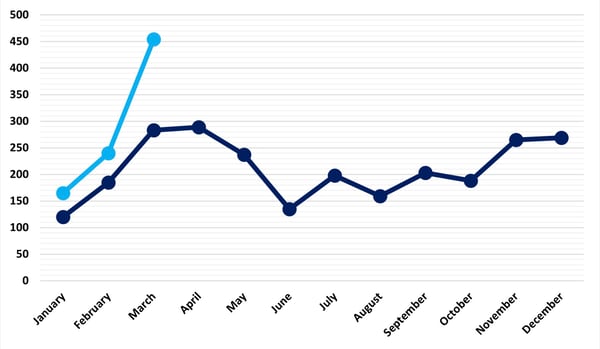 Global Ransomware Attacks by Month
Global Ransomware Attacks by Month
Source: NCC Group
The industrial sector was the most targeted in March, experiencing 32% of the attacks, with more expected sectors like finance and healthcare falling lower in the sector list.
While Cl0p ransomware (RWaaS variant that leveraged a vulnerability in GOAnywhere Managed File Transfer) dominated the growth, Lockbit 3.0 was a close second. I’ve highlighted Lockbit before, mostly because they continue to use phishing attacks as their initial attack vector.
The growth we’re seeing in ransomware attacks, along with the continued use of phishing attacks, should be enough to make organizations realize they need better protective measures in place – which should include Security Awareness Training – to reduce the effectiveness of phishing emails used as the first step in ransomware attacks.
Free Ransomware Simulator Tool
Threat actors are constantly coming out with new strains to evade detection. Is your network effective in blocking all of them when employees fall for social engineering attacks?
KnowBe4’s “RanSim” gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 22 ransomware infection scenarios and 1 cryptomining infection scenario and show you if a workstation is vulnerable.
Here’s how it works:
- 100% harmless simulation of real ransomware and cryptomining infections
- Does not use any of your own files
- Tests 23 types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/ransomware-simulator-tool-partner?partnerid=001a000001lWEoJAAW

