Ransomware Gang Creates “User-Friendly” Stolen Data Search Site for Employee Victims

In an interesting extortion twist to get ransomware victims to pay up, one gang has created a search site to allow employees to see if their own private information has been made public.
Traditionally, ransomware gangs have used stolen data to extort their victim into paying the ransom. Because the data taken is in the tens of hundreds of gigabytes, the historically normal practice has been to slowly leak out the data, making it accessible to whoever decides to visit the ransomware gang’s data publication site.
But, like any business model that’s not working, sometimes it takes a bit of innovation and evolution of the execution to secure the desired outcome. As is the case with the newest – and, reportedly, the most sophisticated – ransomware “kid” on the block, AlphV/BlackCat ransomware.
According to BleepingComputer, this gang has shied away from the traditional extortion techniques and instead built out a relatively user-friendly website that allows employees of the victim organization to search through the stolen data to see if their personal data is included.
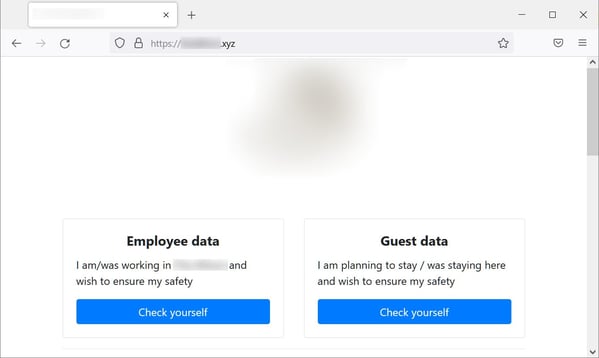
Source: Bleeping Computer
This technique feels like it would add some pressure onto the organization to pay to have this site taken down (in addition to the leaking of all the data, etc.).
This kind of evolution in innovative ransomware techniques (and more like it) should be expected, as ransomware isn’t going anywhere anytime soon. This means your organization needs to put the necessary effort into keeping ransomware from making its’ way onto your network. This effort should include the organization’s user base who, with the right Security Awareness Training, can help augment your security stance and lower the likelihood that ransomware will successfully strike.
Free Ransomware Simulator Tool
Threat actors are constantly coming out with new strains to evade detection. Is your network effective in blocking all of them when employees fall for social engineering attacks?
KnowBe4’s “RanSim” gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 22 ransomware infection scenarios and 1 cryptomining infection scenario and show you if a workstation is vulnerable.
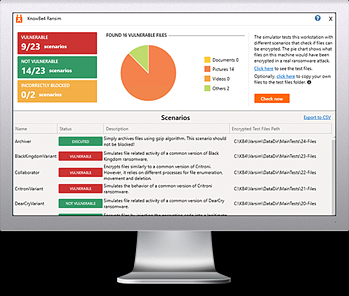
Here’s how it works:
- 100% harmless simulation of real ransomware and cryptomining infections
- Does not use any of your own files
- Tests 23 types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/ransomware-simulator-tool-partner?partnerid=001a000001lWEoJAAW

