Social Engineering Seeks Okta Credentials

Identity and authentication management provider Okta has warned of social engineering attacks that are targeting IT workers in an attempt to gain administrative privileges within organizations’ networks.
“In recent weeks, multiple US-based Okta customers have reported a consistent pattern of social engineering attacks against IT service desk personnel, in which the caller’s strategy was to convince service desk personnel to reset all Multi-Factor Authentication (MFA) factors enrolled by highly privileged users,” Okta says. “The attackers then leveraged their compromise of highly privileged Okta Super Administrator accounts to abuse legitimate identity federation features that enabled them to impersonate users within the compromised organization.”
The threat actors already had some information about the targeted organizations before they contacted the IT employees
“Threat actors appeared to either have a) passwords to privileged user accounts or b) be able to manipulate the delegated authentication flow via Active Directory (AD) prior to calling the IT service desk at a targeted org, requesting a reset of all MFA factors in the target account,” Okta says. “In the case of Okta customers, the threat actor targeted users assigned with Super Administrator permissions.”
The attackers also impersonated another identity management provider using a phony app.
“The threat actor was observed configuring a second Identity Provider (IdP) to act as an ‘impersonation app’ to access applications within the compromised Org on behalf of other users,” the company says. “This second Identity Provider, also controlled by the attacker, would act as a ‘source’ IdP in an inbound federation relationship (sometimes called ‘Org2Org’) with the target. From this ‘source’ IdP, the threat actor manipulated the username parameter for targeted users in the second ‘source’ Identity Provider to match a real user in the compromised ‘target’ Identity Provider. This provided the ability to Single sign-on (SSO) into applications in the target IdP as the targeted user.”
New-school security awareness training can teach your employees to recognize social engineering tactics so they can thwart targeted attacks.
Okta has the story.
he story.
Free Phishing Security Test
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
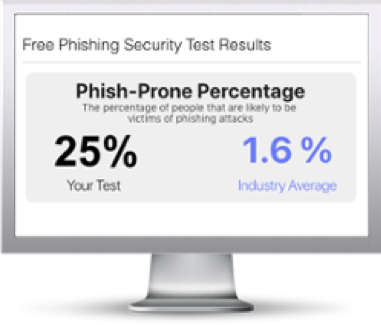
Here’s how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/phishing-security-test-partner?partnerid=001a000001lWEoJAAW

