TeamViewer Network Breached as Russian APT29 Hackers Strike Again

In a concerning development, TeamViewer, one of the world’s leading remote access software providers, has disclosed a cyber attack that breached its corporate network environment.
The incident was first detected on June 26, 2024, when TeamViewer’s security team identified irregularities in their internal IT infrastructure.
Responding swiftly, TeamViewer activated its incident response procedures and engaged renowned cybersecurity experts to investigate and mitigate the breach. While details are still emerging, TeamViewer attributes the attack to APT29, a notorious Russian state-sponsored hacking group with a track record of sophisticated cyber espionage campaigns.
The cybersecurity firm NCC Group has issued an alert warning its customers about a “significant compromise of the TeamViewer remote access and support platform by an APT group.” Furthermore, Health-ISAC, an intelligence-sharing community for healthcare organizations, cautioned that APT29 is actively exploiting TeamViewer connections.
Although TeamViewer has stated that there is no evidence of the product environment or customer data being affected, the implications of this breach are far-reaching. With over 640,000 customers worldwide and installations on 2.5 billion devices, TeamViewer’s remote access capabilities could potentially provide threat actors with a foothold into countless networks.
This incident serves as a stark reminder of the persistent and evolving cyber threats that organizations face, even from seemingly secure and trusted software solutions. Threat actors are continuously adapting their tactics, exploiting new vulnerabilities, and leveraging sophisticated hacking tools to compromise systems and exfiltrate sensitive data.
As the investigation into the TeamViewer breach continues, we urge organizations to remain vigilant, review their remote access protocols, and prioritize ongoing security awareness training initiatives. Cyber threats are constantly evolving, and a well-informed and prepared workforce is often the last line of defense against extremely expensive breaches.
KnowBe4 empowers your workforce to make smarter security decisions every day. Over 65,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.
Bleeping Computer has the full story.
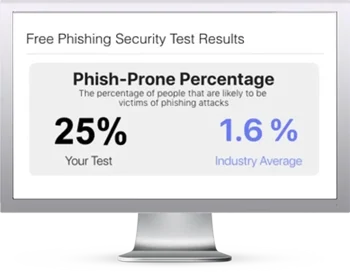
Free Phishing Security Test
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Here’s how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/phishing-security-test-partner?partnerid=001a000001lWEoJAAW

