The International Joint Commission Falls Victim to Ransomware Attack; 80GB Of Data Stolen
The International Joint Commission (ICJ), an organization that handles water issues along the Canada–United States border, was hit by a ransomware attack, the Register reports.
The Commission said in a statement, “The International Joint Commission has experienced a cyber security incident. The organization is taking measures to investigate and resolve the situation.”
The Commission hasn’t disclosed many details, but the NoEscape ransomware gang claimed responsibility for the attack. The group says it’s stolen 80GB of sensitive data from the organization, and will begin leaking it if the ransom isn’t paid.
“On September 7, the NoEscape ransomware crew listed IJC as a victim on its dark-web site, and claimed it breached the commission’s network, and then stole and encrypted a flood of confidential data,” the Register says. “This info, according to the crooks, included contracts and legal documents, personal details belonging to employees and members, financial and insurance information, geological files, and much other confidential and sensitive information.’”
NoEscape said in its leak notice, “If management continues to remain silent and does not take the step to negotiate with us, all data will be published. We have more than 50,000 confidential files, and if they become public, a new wave of problems will be colossal. For now, we will not disclose this data or operate with it, but if you continue to lie further, you know what awaits you.”
Most ransomware attacks begin with some form of social engineering, such as tricking an employee into opening a malicious attachment delivered in a phishing email. New-school security awareness training can give your organization an essential layer of defense by teaching your employees how to thwart social engineering tactics.
The Register has the story.
Free Ransomware Simulator Tool
Threat actors are constantly coming out with new strains to evade detection. Is your network effective in blocking all of them when employees fall for social engineering attacks?
KnowBe4’s “RanSim” gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 24 ransomware infection scenarios and 1 cryptomining infection scenario and show you if a workstation is vulnerable.
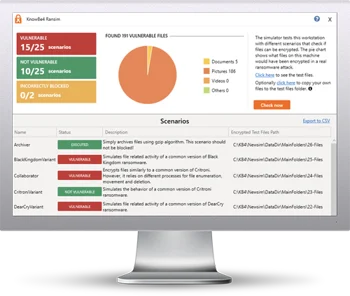
Here’s how it works:
- 100% harmless simulation of real ransomware and cryptomining infections
- Does not use any of your own files
- Tests 25 types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/ransomware-simulator-tool-partner?partnerid=001a000001lWEoJAAW

