There Is A Whole New Type of Blockchain Scam Called “Ice phishing”
In a post Wednesday last week, Microsoft issued a warning that they are seeing a brand new type of blockchain-centric attack aimed at web3 — a term used to describe the decentralized environment created on the blockchain.
The post by the Microsoft 365 Defender Research Team analyzed the recent Badger DAO attack, which stole more than $120 million from blockchain users November and December last year.
They warned that these attacks are on the rise: “There are multiple types of phishing attacks in the web3 world,” wrote Christian Seifert, member of the Microsoft 365 Defender Research Team. “The technology is still nascent, and new types of attacks may emerge.”
Ice fishing involves cutting a hole in a frozen body of water in order to catch fish. Ice phishing, as the Defender team has coined it, uses social engineering to trick a user into signing a transaction that delegates approval of the user’s tokens to the attacker, it doesn’t involve stealing one’s private keys.
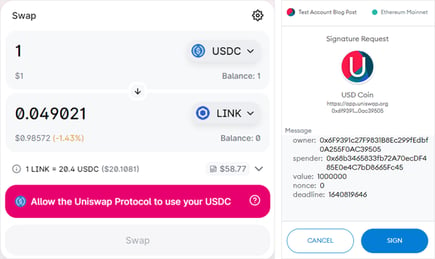
The attack corrupts a common type of transaction that enables interactions with DeFi smart contracts, as those are used to interact with the user’s tokens (e.g., swaps)….In an ‘ice phishing’ attack, the attacker merely needs to modify the spender address to attacker’s address.
This can be quite effective as the user interface doesn’t show all pertinent information that can indicate that the transaction has been tampered with….Once the approval transaction has been signed, submitted, and mined, the spender can access the funds. In case of an ‘ice phishing’ attack, the attacker can accumulate approvals over a period of time and then drain all victim’s wallets quickly.”
This is the original post by Redmond, and it’s quite interesting reading! https://www.microsoft.com/security/blog/2022/02/16/ice-phishing-on-the-blockchain/
Request A Demo: Security Awareness Training

New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn’t a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4’s security awareness training and simulated phishing platform and see how easy it can be!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/one-on-one-demo-partners?partnerid=001a000001lWEoJAAW

