This Scary Strain of Sleeper Ransomware Is Really a Data Wiper in Disguise

This Data wiper replaces every other 666 bytes of data with junk. Techradar reported that a new data-wiping malware has been detected, infecting more and more endpoints with each passing day – but what’s most curious is that it poses as ransomware.
The malware is called Azov Ransomware, and when run on a victim’s device, it overwrites file data with junk, rendering the files useless. The overwrites are cyclical – the malware would overwrite 666 bytes of data, then leave the next 666 intact, then repeat the process.
Even though there is no way to retrieve the corrupt files, there is no decryption key or ransom demands, the malware(opens in new tab) still comes with a ransom note, which says that victims should reach out to security researchers and journalists for help.
It’s a Sleeper Program That Wakes up October 27th
Another curious thing about Azov Ransomware is that it comes with a trigger, having it sit idly on the endpoint until October 27, 10:14:30 AM UTC, after which all hell breaks loose. When this date comes, the victim doesn’t necessarily need to run the exact executable – running pretty much any program will do. That’s because the wiper will infect all other 64-bit executables on the devices whose file path does not hold specific strings.
SOURCE: TechRadar
Free Ransomware Simulator Tool
Threat actors are constantly coming out with new strains to evade detection. Is your network effective in blocking all of them when employees fall for social engineering attacks?
KnowBe4’s “RanSim” gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 22 ransomware infection scenarios and 1 cryptomining infection scenario and show you if a workstation is vulnerable.
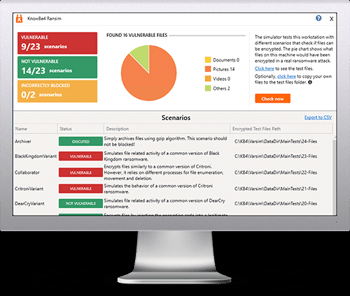
Here’s how it works:
- 100% harmless simulation of real ransomware and cryptomining infections
- Does not use any of your own files
- Tests 23 types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/ransomware-simulator-tool-partner?partnerid=001a000001lWEoJAAW

