Three-Quarters of Ethical Hackers Can Collect and (Potentially) Exfiltrate Data in 10 Hours or Less

New insight from the SANS Institute surveying 300 ethical hackers sheds some light on how they perceive your security stance – and how easy it is for them to break in despite your efforts.
Most of the reports I cover here are either based on organization’s experienced with attacks, or their concerns about future attacks. Rarely do we get to see into the mind of the hacker themselves and understand just how simple they see an environment is to break into.
The 2022 SANS Survey Report: Inside the Minds & Methods of Modern Adversaries put out by SANS and security vendor BishopFox gives us a glimpse into the mind of a hacker, allowing us to see our own environment cybersecurity through their eyes. In this case 300 ethical hackers who were happy to share their view of organizational cybersecurity today. According to the report:
- 37% of hackers believe that they can break into an environment more often than not, if not always
- 57% stated they could successfully discover an exploitable exposure in 10 hours or less
- Nearly 64% state they only need five hours or less to collect and potentially exfiltrate data, with 74% needing 10 hours or less
- Nearly half (49.3%) state that social engineering and phishing attacks are the attack vectors that have the greatest “return on investment”
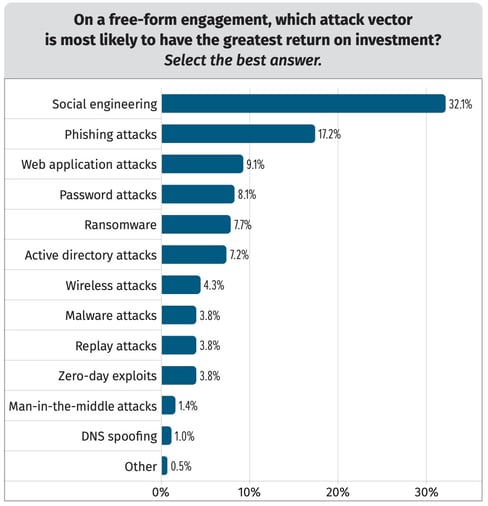
Source: SANS
This last stat alone highlights the need for users to play a role in you organization’s security stance. Hackers will find vulnerabilities and exploits (of which, can include your users falling for social engineering scams), so it makes sense that you need to educate users with Security Awareness Training so they don’t assist the hacker who already has made it clear they can easily get in. By shoring up this part of your defenses, it’s less likely hackers will get a foothold within your organization.
Request A Demo: Security Awareness Training
New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn’t a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4’s security awareness training and simulated phishing platform and see how easy it can be!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/one-on-one-demo-partners?partnerid=001a000001lWEoJAAW

