Vendor Email Compromise Attacks Use the Same Playbook for Multiple Attacks

Seeking very large paydays, Vendor Email Compromise (VEC) threat actors are finding out what works and repurposing their content and processes to increase chances of seeing a massive payout.
VEC is a form of Business Email Compromise (BEC) where an email account isn’t just impersonated (e.g., using someone’s name, a lookalike domain, etc.) but actually compromising credentials and taking over an account of someone within an organization. By doing this, the deliverability of email is nearly guaranteed, as is the credibility of the email being sent – since it actually comes from the impersonated employee’s employer.
According to new findings by security researchers at Abnormal Security, several VEC attacks have been spotted targeting critical infrastructure and repeatedly using the same emails and tactics across multiple victim organizations. The attack is simple – one or more emails that seek to have any outstanding invoices paid to a different bank account, as shown below:
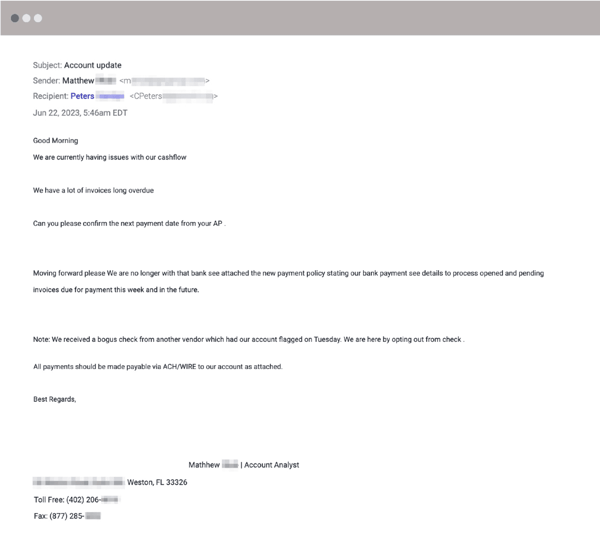
According to Abnormal Security, the most effective tactic in this attack is the use of a known domain. It makes even a vigilant employee (who checks the “From” address, etc.) to think the email is legitimate. It’s only those users that have been taught through security awareness training and good security policies that anytime a change of payment details is requested, there needs to be a verification step using another medium and a known means of contact (instead of any contact details within the email in question) to validate the request.
Can hackers spoof an email address of your own domain?

Are you aware that one of the first things hackers try is to see if they can spoof the email address of your CEO? If they are able to commit “CEO Fraud”, penetrating your network is like taking candy from a baby.
Now they can launch a “CEO fraud” spear phishing attack on your organization, and that type of attack is very hard to defend against, unless your users are highly ‘security awareness’ trained.
Find out now if your domain can be spoofed. The Domain Spoof Test (DST) is a one-time free service. Run this test so you can address any mail server configuration issues that are found.
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/domain-spoof-test-partner?partnerid=001a000001lWEoJAAW

