Warning Customers About Social Engineering.

It’s a familiar story: scam artists impersonate a trusted brand, a trusted business or a trusted authority in emails and on bogus sites designed to exploit that very trust to commit fraud. Generally, this isn’t the fault of the person or organization being impersonated. But it’s worth remembering that there are practices and policies an organization can take to help keep their customers and other stakeholders protected from this kind of fraud.
There was an example of this recently from the cryptocurrency sector. The hardware crypto wallet provider Trezor warned its customers that there was an active phishing campaign in progress in which crooks were pretending to be Trezor in an attempt to steal users’ private keys.
“The phishing campaign involves attackers posing as Trezor and contacting victims via phone calls, texts or emails claiming that there has been a security breach or suspicious activity on their Trezor account,” Cointelegraph writes.
“‘Trezor Suite has recently endured a security breach, assume all your assets are vulnerable,” the fake message reads, inviting users to follow a phishing link to ‘secure’ their Trezor device.
“‘Please ignore these messages as they are not from Trezor,’ Trezor declared on Twitter, emphasizing that the firm will never contact its customers via calls or SMS. The firm added that Trezor had not found any evidence of a database breach.”
Trezor, of course, hadn’t sustained a security breach. It was just phishbait the scammers were dangling in front of their marks.
It’s a useful reminder and a good example of how to warn customers. It’s also good policy to make your customers aware that you’re not going to send them links, not by call, text or email. New-school security awareness training can help you and your employees develop the kinds of security practices and policies that will help not only them, but your customers as well.
Cointelegraph has the story.
Free Phishing Security Test
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
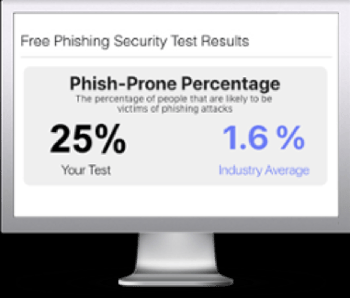
Here’s how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/phishing-security-test-partner?partnerid=001a000001lWEoJAAW

