Cybersecurity Experts Weigh in on Modern Email Attacks

Abnormal Security’s CISO, Mike Britton consolidates some of the best advice from a three-part webinar series on the current state of risk found in email-based cyberattacks
The threat of email attacks today is so great, it took Abnormal Security three separate webinars just to cover it (and I’d wager they only scratched the surface). In a recent blog, Mike Britton provides the highlights and major takeaways from that webinar series to bring you the nuggets of wisdom that will have a real impact on your cybersecurity strategy’s focus and execution around stopping email-based attacks.
Here are a few of the pearls I pulled from that article:
- Modern threat actors do extensive research on their targets, creating convincing emails that trick employees.
- Compromised credentials (a focus of most phishing campaigns today) provides the threat actor with an ability to access other applications, reset passwords for other accounts, and can act as the basis for launching additional attacks.
- Email will continue to be a primary attack vector for ransomware, because of the breadth of abilities threat actors have to trick recipients into opening attachments.
- Stopping attacks is a shared responsibility. Troy Hunt (of Have I Been Pwned? Fame) said that “requiring employees to complete ongoing security awareness training can help them identify malicious emails that are usually the first step in attacks.”
Take a look at the longer list of key takeaways and realize that anytime email is involved in an attack, so are your users – making it necessary to enroll every one of them in Security Awareness Training to they can play their part in stopping email-based cyberattacks.
Find out which of your users’ emails are exposed before bad actors do.
Many of the email addresses and identities of your organization are exposed on the internet and easy to find for cybercriminals. With that email attack surface, they can launch social engineering, spear phishing and ransomware attacks on your organization. KnowBe4’s Email Exposure Check Pro (EEC) identifies the at-risk users in your organization by crawling business social media information and now thousands of breach databases.
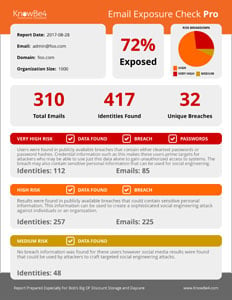
Here’s how it works:
- The first stage does deep web searches to find any publicly available organizational data
- The second stage finds any users that have had their account information exposed in any of several thousand breaches
- You will get a summary report PDF as well as a link to the full detailed report
- Results in minutes!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/email-exposure-check-pro-partner?partnerid=001a000001lWEoJAAW

