New Phishing-as-a-Service (PhaaS) platform, ‘Tycoon 2FA’, Targets Microsoft 365 and Gmail Accounts

A new PhaaS service brings the power of bypassing multi-factor authentication (MFA) to the world’s most-used email platforms.
At its core, Tycoon 2FA isn’t doing anything new. It uses a reverse proxy server to host a phishing web page that impersonates the legitimate email platform in question. Then it intercepts the victim’s input and relays them to the legitimate service.
But it’s how this platform does it that is sophisticated. In a deep dive analysis of the phishing kit by security vendor Sekoia, we get a glimpse into just how sophisticated and much work goes into this latest iteration of the PhaaS platform.
Check out the following diagram and to understand how it bypasses 2FA without letting the victim know.
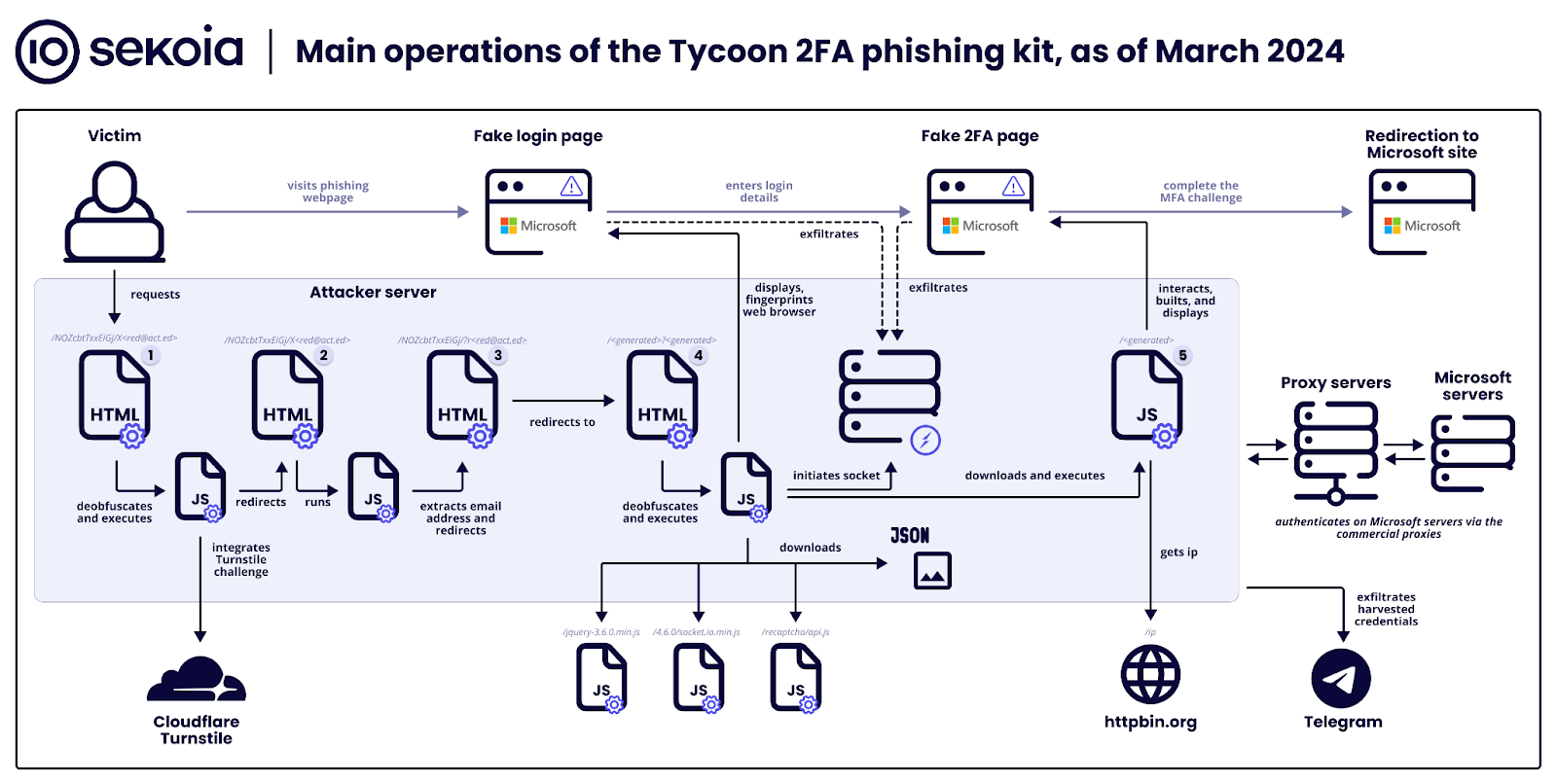
Source: Sekoia
According to Bleeping Computer’s coverage of the Sekoia analysis, there are seven stages in this attack:
- Stage 0 – Attackers distribute malicious links via emails with embedded URLs or QR codes, tricking victims into accessing phishing pages.
- Stage 1 – A security challenge (Cloudflare Turnstile) filters out bots, allowing only human interactions to proceed to the deceptive phishing site.
- Stage 2 – Background scripts extract the victim’s email from the URL to customize the phishing attack.
- Stage 3 – Users are quietly redirected to another part of the phishing site, moving them closer to the fake login page.
- Stage 4 – This stage presents a fake Microsoft login page to steal credentials, using WebSockets for data exfiltration.
- Stage 5 – The kit mimics a 2FA challenge, intercepting the 2FA token or response to bypass security measures.
- Stage 6 – Finally, victims are directed to a legitimate-looking page, obscuring the phishing attack success.
According to Sekoia, Tycoon has received an estimated total of over $394K in bitcoin since the services inception back in 2019. Sekoia estimate that “several hundred Tycoon 2FA kits were sold as-a-service over half a year” since the latter part of 2024, demonstrating that this phishing kit is growing in popularity and effectiveness.
KnowBe4 empowers your workforce to make smarter security decisions every day. Over 65,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.
Free Phishing Security Test
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Here’s how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/phishing-security-test-partner?partnerid=001a000001lWEoJAAW

