Phishing for Ring Customers

INKY warns that a phishing campaign is targeting users of the Ring video security system. The scammers are sending brief phishing emails instructing recipients to click on the attached HTML file in order to update their membership. The file will open a webpage hosted locally on the victim’s machine, which helps the attackers avoid detection by security filters.
The HTML file contains a link to a phishing site that spoofs Ring’s login page, and is designed to harvest the victim’s credentials, credit card information and social security number. After entering their information, the victim will be redirected to Ring’s legitimate website.
INKY notes that users should instantly be wary of the phishing page, since it asks for their social security number.
“After completing the login process, customers are presented with a form to update credit card information,” INKY says. “The form also asks for a social security number, which is suspicious considering vendors rarely ask for your social security number and hardly ever along with credit card information.”
INKY offers the following recommendations to help users avoid falling for these attacks:
- “An account issue can be resolved by visiting a company’s website directly instead of clicking on email attachments and links.”
- “Use your browser’s address bar to confirm that you’re on a website instead of a local file.”
- “Confirm the domain of the website. In this case, recipients should be suspicious that the Ring login page is hosted on immobilmedia.com instead of ring.com.”
- “Be careful with display name spoofing. This example uses ‘Ring Video Doorbell’ as the display name, but recipients should be suspicious that the sender’s email address isn’t an authentic Ring email address.”
- “Always be suspicious when receiving HTML attachments from unknown senders. Simply opening the file can run malicious code on the recipient’s computer.”
New-school security awareness training can enable your employees to recognize the signs of phishing and other social engineering attacks.
INKY has the story.
Free Phishing Security Test
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
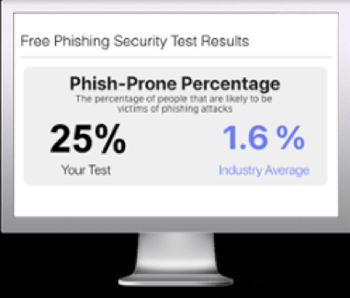
Here’s how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/phishing-security-test-partner?partnerid=001a000001lWEoJAAW

